Best Practices for SPF, DKIM, and DMARC Records
Email authentication ensures your emails reach inboxes and protect your domain from phishing and spoofing. Here's how SPF, DKIM, and DMARC work together to safeguard your email system:
- SPF: Authorizes specific servers to send emails for your domain.
- DKIM: Adds a digital signature to verify email integrity.
- DMARC: Enforces policies for handling emails that fail SPF/DKIM checks and provides detailed reports.
Key Takeaways:
- SPF: Keep records concise (under 10 DNS lookups) and test changes before enforcing strict policies.
- DKIM: Use strong keys (2048-bit), rotate them periodically, and align with your domain.
- DMARC: Start with a monitoring policy (
p=none), analyze reports, and gradually enforce stricter rules (quarantine→reject).
Tools like Mailforge simplify managing multiple domains, automate DNS updates, and monitor email performance. Regular testing and adherence to email laws like CAN-SPAM are critical for maintaining deliverability and protecting your brand.
Next Steps:
- Audit your SPF, DKIM, and DMARC setup.
- Use tools like Mailforge for automation and monitoring.
- Review DMARC reports regularly to refine your policies.
Setting Up SPF Records for Better Deliverability
How SPF Records Work
SPF (Sender Policy Framework) records are a crucial part of email authentication, helping to protect your domain from spoofing and phishing attempts. Essentially, an SPF record is a list of servers and IP addresses authorized to send emails on behalf of your domain.
Here’s how it works: when an email server receives a message claiming to come from your domain, it checks your domain's DNS for the SPF record. If the sending server's IP address matches an authorized source listed in the record, the email passes SPF authentication. If it doesn’t match, the email fails. Based on this result - and other factors - the receiving server decides whether to deliver the email to the inbox, send it to spam, or reject it altogether.
SPF records are stored as TXT entries in your domain's DNS settings. They use a specific syntax to define which servers can send emails and what actions to take with unauthorized attempts.
SPF Best Practices
To make the most of SPF records while ensuring smooth email delivery, follow these guidelines:
- Stay within the DNS query limit. SPF records allow a maximum of 10 DNS lookups. Each "include" statement in your record counts toward this limit. Exceeding it will cause SPF to fail, which could block your emails. Consolidate records where possible to avoid hitting the limit.
-
End with
-allor~all. Avoid using+allas it allows any server to send emails on your behalf, defeating the purpose of SPF. Use-allfor strict enforcement, or start with~all(soft fail) during testing phases. - Include only trusted sources. Limit your SPF record to the email servers and services you actively use, such as your email hosting provider, marketing platforms (e.g., Mailchimp, Constant Contact), or CRM systems. Regularly review and update your record to remove outdated services.
- Use IP addresses when applicable. Specifying IP addresses instead of hostnames can reduce DNS lookups and improve efficiency. However, only use this approach if you’re confident the IP addresses won’t change frequently.
-
Test before making changes. Misconfigured SPF records can disrupt email delivery. Use SPF testing tools to validate your record before publishing it. Start with
~allto monitor how your record performs, and switch to-allonce you’re sure everything is working correctly. - Monitor authentication results. Set up DMARC reporting to track SPF pass and fail rates. This helps you spot unauthorized senders or misconfigurations early, minimizing potential issues with deliverability.
For businesses managing multiple domains, tools like Mailforge can simplify SPF configuration, ensuring consistency and preventing errors like exceeding the DNS lookup limit.
How to Add an SPF Record
Adding an SPF record is straightforward and involves creating a TXT record in your domain's DNS. While the steps vary slightly depending on your DNS provider, the general process is as follows:
Step 1: Access your DNS management panel.
Log into your domain registrar or DNS hosting provider’s control panel. Look for options like "DNS Management", "DNS Settings", or "Zone File Editor." Some popular providers in the U.S. include GoDaddy, Namecheap, Cloudflare, and Route 53.
Step 2: Build your SPF record.
Start your record with v=spf1, followed by the authorized senders. For example:
v=spf1 include:_spf.google.com include:mailgun.org -all
This example authorizes Google Workspace and Mailgun to send emails for your domain while rejecting all other sources.
Step 3: Add the TXT record.
Create a new TXT record. Set the hostname to "@" (representing your root domain) or leave it blank, depending on your provider's instructions. Paste your SPF record into the value field. Use a TTL (Time To Live) of 3600 seconds (1 hour) or your provider's default.
Step 4: Save and verify.
Save your changes and wait for DNS propagation, which typically takes 15–30 minutes but can sometimes take up to 24 hours. Use online SPF lookup tools to confirm your record is correctly published and valid.
Step 5: Test email delivery.
Send test emails from your authorized sources to various email providers like Gmail, Outlook, and Yahoo. Check the email headers to ensure SPF authentication is passing.
Keep in mind that each domain can only have one SPF record. If you already have one, update the existing record instead of creating a new one. Multiple SPF records will cause authentication to fail.
With SPF configured, you’re one step closer to securing your email system. Platforms like Mailforge can automatically manage SPF setup for multiple domains, saving time and avoiding manual errors. Next, consider adding DKIM to further enhance your email security.
DKIM Setup and Key Management
How DKIM Works
DKIM, or DomainKeys Identified Mail, adds a layer of security to your emails by attaching a cryptographic signature. This signature ensures two things: the email genuinely came from your domain and hasn't been tampered with during transit. Essentially, it acts as a digital "seal of authenticity" for your messages.
Here’s how it works: DKIM uses a pair of cryptographic keys - a private key and a public key. Your email server keeps the private key secure, while the public key is published in your domain's DNS records. When an email is sent, your server uses the private key to create a unique digital signature based on specific email headers and the content. This signature is then added to the email as a DKIM header.
On the recipient's side, their server retrieves your public key from DNS and checks the signature. If the signature matches, the email is verified as authentic and intact. If it doesn’t, the email could be flagged as suspicious or sent to the spam folder.
While SPF validates which servers are allowed to send emails on behalf of your domain, DKIM focuses on verifying the integrity of the message and confirming the sender's identity.
DKIM Best Practices
To get the most out of DKIM, follow these key practices:
- Use Strong Keys: Opt for 2048-bit RSA keys to ensure robust protection against potential attacks.
- Rotate Keys Regularly: Periodically update your keys to maintain security. If you suspect a compromise, update immediately, ensuring the new public key is added to your DNS before switching.
- Sign Essential Headers: Always sign critical headers, especially the "From" header, to enhance verification and support DMARC alignment.
- Separate Selectors for Different Streams: Use distinct selectors and DKIM keys for different email streams (e.g., transactional, marketing, and internal emails). This simplifies management and limits the impact if one key is compromised.
- Align with the From Domain: Configure your DKIM signing domain to match the domain in the "From" address. This alignment supports DMARC compliance and helps boost your sender reputation.
If your business manages multiple domains or large-scale email operations, tools like Mailforge can help automate DKIM setup and key management, reducing manual errors and ensuring consistency.
How to Configure DKIM
Setting up DKIM involves a few straightforward steps:
-
Generate a DKIM Key Pair
Use your email server’s tools or an online generator to create a DKIM key pair. If you’re using platforms like Google Workspace or Microsoft 365, they provide built-in tools for generating and managing DKIM keys. -
Choose a Selector and Follow Provider Instructions
Follow your email provider’s DKIM setup guide. Select a short identifier, known as a selector, to differentiate between multiple DKIM keys for your domain. Common selectors include terms like "default", "mail", or even date-based names like "2024sep." -
Publish the Public Key in DNS
Add a TXT record to your DNS with the format:
[selector]._domainkey.[yourdomain.com]
For example, if your selector is "mail" and your domain is "company.com", the record would be:
mail._domainkey.company.com
The record value should start withv=DKIM1; k=rsa; p=followed by your encoded public key. -
Test Your Setup
Use online DKIM validators to check your configuration and verify email headers to ensure the signature is being added correctly. -
Configure Your Email Server
Update your email server settings to sign outgoing messages with the private key. Since setup steps vary by system, refer to your server’s documentation for guidance. -
Monitor Email Performance
After enabling DKIM, keep an eye on email delivery and spam filtering to ensure signatures are being recognized and emails are reaching inboxes.
Setting Up and Monitoring DMARC Policies
How DMARC Policies Work
After setting up SPF and DKIM, DMARC (Domain-based Message Authentication, Reporting & Conformance) takes your email authentication strategy to the next level. Acting as a policy enforcer, DMARC tells receiving mail servers what to do with messages that fail SPF or DKIM checks. While SPF and DKIM handle the authentication process, DMARC focuses on managing suspicious emails and providing detailed reports on authentication attempts.
The key to DMARC lies in alignment. For SPF, the domain in the MAIL FROM (envelope sender) must match the domain in the From header. For DKIM, the signing domain (found in the d= value of the DKIM signature) must align with the domain in the From address. A message passes DMARC validation if either SPF or DKIM succeeds with proper alignment. If both fail, the DMARC policy determines the next steps.
To implement DMARC, you need to publish it as a TXT record in your domain’s DNS. This helps email providers identify legitimate emails and block fraudulent ones, significantly reducing risks like phishing and spoofing. Providers like Google and Yahoo actively check for DMARC records, and domains without them may experience delivery problems or have emails marked as spam.
DMARC also offers a reporting feature that provides insights into your email authentication performance. These reports highlight emails that pass or fail, helping you quickly detect security threats or configuration issues that could harm deliverability.
Now that the purpose of DMARC is clear, let’s explore how to implement it effectively.
DMARC Best Practices
Getting DMARC right requires a careful, step-by-step approach. Start with a monitoring-only policy (p=none) to gather data without affecting email delivery. During this phase, use the aggregate and forensic reports to understand authentication patterns and identify any issues with legitimate email sources.
Once your setup is validated and legitimate emails are authenticated correctly, you can gradually move to stricter policies. Begin with a quarantine policy to send suspicious emails to spam folders. Over time, transition to a reject policy, which blocks emails that fail DMARC checks. Make these changes incrementally to ensure legitimate emails aren’t mistakenly blocked.
Monitoring your DMARC reports regularly is essential. These reports help you spot and resolve persistent issues, strengthening your overall email security setup.
If you manage multiple domains or have a complex email system, tools like Mailforge can simplify the process. They automate DNS configurations and provide centralized monitoring, making DMARC management much easier.
Ready to set up your DMARC record? Follow these steps.
How to Add a DMARC Record
Before adding a DMARC record, ensure your SPF and DKIM records are correctly configured and have been working for at least 48 hours.
-
Check for Existing Records: Use a DNS lookup tool or a command-line utility like
nslookupto see if a DMARC record already exists. Each domain can only have one DMARC record, so duplicates can cause failures. -
Create the DMARC Record: Log in to your DNS management platform and add a new TXT record with the following details:
- Record Type: TXT
-
Name/Host:
_dmarc(some platforms automatically append your domain name) -
Value: Use this example:
v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.com
v=DMARC1: Indicates the DMARC version.p=none: Sets the policy to monitoring mode.rua=: Specifies the email address for aggregate reports.
ruf=mailto:dmarc@yourdomain.com: Enables forensic reports for detailed failure analysis.pct=: Defines the percentage of emails the policy applies to.
- Verify and Test: After saving the record, use an online DMARC validator or a DNS lookup tool to confirm its accuracy. Allow up to 24 hours for DNS changes to propagate.
- Monitor and Adjust: During the initial phase, closely review DMARC reports. Use these insights to refine your SPF and DKIM setups and adjust DMARC policies before enforcing stricter rules.
Scaling Email Infrastructure with Automation
When handling large-scale email operations, automating DNS management becomes critical, especially when robust authentication is already in place.
Managing Multiple Domains
Handling email authentication for multiple domains can quickly get overwhelming without a centralized system. Each domain requires its own authentication records, and keeping these consistent across dozens - or even hundreds - of domains is nearly impossible to do manually.
Every domain needs regular updates and close monitoring. A single misstep, like a misconfigured record, can cause deliverability issues for an entire domain, impacting all associated mailboxes. Additionally, businesses often encounter record conflicts. For instance, using different SPF records for subdomains or failing to update DKIM keys after rotation can lead to authentication errors. These problems don’t just hurt deliverability - they can also trigger spam filters and harm your sender reputation.
When scaling beyond a handful of domains, centralized management is no longer optional. Without it, you risk wasting hours manually updating DNS records, keeping tabs on authentication statuses, and troubleshooting delivery problems.
Using Mailforge for Scalable Email Infrastructure
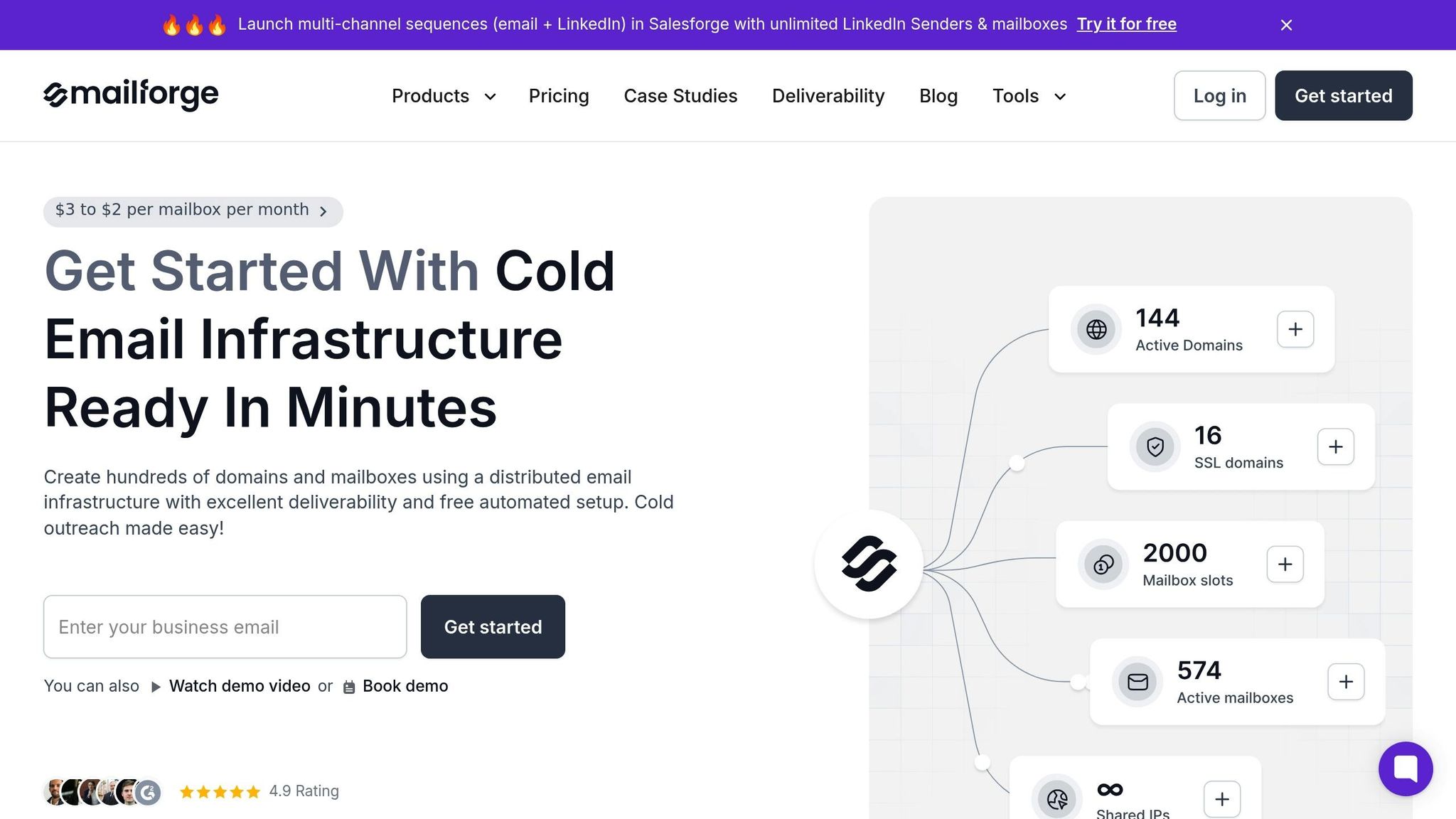
Mailforge simplifies these challenges by automating DNS setup, reducing the chances of manual configuration errors. With Mailforge, you can manage hundreds - or even thousands - of domains and mailboxes in just minutes, thanks to its automated technical configurations.
One standout feature is bulk DNS updates. Instead of updating each domain one at a time, you can apply changes across your entire infrastructure simultaneously. This not only ensures consistency but also slashes the time spent on maintenance.
Mailforge also includes SSL and domain masking features to enhance security and maintain a polished, professional appearance in recipient inboxes. These tools protect your domains from vulnerabilities while ensuring your emails look credible.
For businesses in the US, Mailforge offers premium deliverability features to help maximize inbox placement. Plus, its compatibility with any sending software ensures you’re not tied to a specific platform, allowing you to integrate it seamlessly into your existing workflows. This flexibility ensures smooth operations and sets the foundation for cohesive performance across your Forge Stack.
Integrating Mailforge with Other Forge Stack Products
Mailforge becomes even more powerful when combined with other Forge Stack solutions like Salesforge, Warmforge, Infraforge, Primeforge, and Leadsforge, creating a unified and scalable email infrastructure.
Warmforge complements Mailforge by providing email warm-up services and deliverability testing. Since email authentication is only one part of ensuring strong deliverability, Warmforge helps new domains and mailboxes gradually build a solid sender reputation.
For businesses needing private email infrastructure, Infraforge offers advanced solutions like multi-IP provisioning and API access for enterprise-level customization. Meanwhile, Primeforge delivers Google Workspace and Microsoft 365 mailboxes with US IP addresses, enabling businesses to maintain professional email standards while scaling their outreach.
Each Forge product adds value to your email outreach strategy. Salesforge handles sequencing, and Leadsforge focuses on lead generation, ensuring an efficient and scalable email ecosystem. While all Forge Stack products integrate seamlessly, they’re available as separate subscriptions, so you can choose only the tools your business requires while enjoying the benefits of a fully connected suite.
Maintenance and Compliance
Keeping your email authentication in top shape isn’t a one-and-done task. It requires consistent attention to ensure everything runs smoothly and stays compliant with legal standards.
Regular Testing and Updates
To maintain accurate records, leverage tools like MxToolbox, DMARCian, or Postmark. These tools help verify the accuracy of your email authentication records, and you’ll need to update them whenever you change or add email providers.
DMARC reports are a goldmine of insights into your email performance. They reveal which messages pass or fail authentication checks, making it easier to identify unauthorized sending attempts or configuration problems. Reviewing these reports monthly can help you catch issues early and keep your email security in check. For businesses managing a large number of domains - like those using platforms such as Mailforge - automated monitoring becomes a necessity since manually testing hundreds of domains isn’t realistic.
Beyond technical upkeep, staying compliant with legal standards is just as important.
Following US Email Laws
Strong email authentication doesn’t just improve security - it also helps ensure compliance with laws like the CAN-SPAM Act, which governs commercial emails in the United States.
"The Controlling the Assault of Non-Solicited Pornography And Marketing (CAN-SPAM) Act is another prominent legal act passed in the USA. It has become a gold standard to handle commercial emails around the world. An interesting aspect of the CAN-SPAM Act is that it does not make it necessary for companies to get consent before sending emails. However, every email must have an opt-out mechanism to remain in compliance with the Act." – EngageLab
To comply with the CAN-SPAM Act, your emails must avoid false or misleading information, feature clear and accurate subject lines, disclose when the email is promotional, and include an easy-to-use opt-out option. Unsubscribe requests must also be handled promptly. Following these rules not only keeps you compliant but also strengthens your email authentication setup and protects your sender reputation.
If you’re using third-party marketing tools, keep a close eye on them to ensure they follow CAN-SPAM requirements. Their non-compliance could harm your reputation as a sender.
Regular Review of Email Authentication Policies
Routine reviews are essential for both maintaining technical reliability and safeguarding your brand’s reputation. Plan quarterly audits to verify your records and document any DNS changes.
During these reviews, confirm that all sending domains and subdomains are properly authenticated with SPF, DKIM, and DMARC. Check that your DMARC policy is progressing as intended - from "none" for monitoring, to "quarantine", and eventually to "reject" as your confidence in the setup grows.
For large-scale updates, use tools like Mailforge’s bulk update features, ensuring all changes align with your broader email strategy and compliance goals.
Conclusion
Email authentication is the backbone of reliable email delivery and brand protection. Tools like SPF, DKIM, and DMARC work together to verify the legitimacy of your emails, ensuring they land in inboxes instead of spam folders.
Key Takeaways
The cornerstone of effective email authentication lies in gradual implementation. Start with a monitoring-only DMARC policy and then tighten controls as your setup becomes more refined. This step-by-step approach minimizes the risk of blocking legitimate emails while you optimize your configuration.
- Keep SPF records concise, limiting them to essential sources and ensuring they stay under the 10 DNS lookup limit. Update them promptly with any service changes.
- Rotate DKIM keys every 12-18 months and ensure consistent signing across all domains and subdomains.
- For DMARC policies, start with monitoring, analyze reports, and progressively enforce stricter rules to protect your email ecosystem.
If your business oversees multiple domains, consider leveraging automated solutions to manage your email infrastructure efficiently. As the number of domains grows, manual management becomes impractical.
These strategies will help you fine-tune your email setup for better delivery rates and stronger protection.
Next Steps for Businesses
To strengthen your email infrastructure, take the following steps:
- Audit your current authentication setup. Use tools like MxToolbox or similar DNS verification services to check your SPF, DKIM, and DMARC records. If any records are missing, start with SPF as the foundation.
- Leverage automation for scalability. Platforms like Mailforge simplify DNS setup and bulk updates, making it easier to manage email authentication for multiple domains.
- Integrate with broader email strategies. Use tools such as Warmforge to protect sender reputation through proper email warm-up, and Salesforge to maximize the effectiveness of cold email campaigns using authenticated domains.
- Perform regular maintenance. Review DMARC reports and audit DNS records consistently. This proactive approach helps you avoid small issues that could escalate into major deliverability problems.
FAQs
How do SPF, DKIM, and DMARC work together to improve email security and ensure your messages are delivered?
SPF, DKIM, and DMARC are key email authentication tools that work together to safeguard your domain from spoofing and ensure better email delivery.
- SPF checks if emails are being sent from servers authorized by your domain, preventing unauthorized use.
- DKIM attaches a digital signature to your emails, confirming they haven’t been altered during delivery.
- DMARC uses SPF and DKIM to let you set rules for how email providers should handle messages that fail authentication.
When configured correctly, these protocols help lower the chances of your emails landing in spam folders and strengthen your domain’s credibility. Tools like Mailforge make it easy by automating the setup of SPF, DKIM, and DMARC records, ensuring your email practices meet industry standards for security and deliverability.
How do I move from a DMARC monitoring policy to full enforcement?
To shift from a DMARC monitoring policy (p=none) to full enforcement (p=reject), start by thoroughly analyzing your email traffic with DMARC reports. These reports are essential for spotting authentication failures and verifying that all legitimate emails align correctly with SPF and DKIM standards.
Take a step-by-step approach by transitioning from p=none to p=quarantine first. This intermediate stage lets you observe how unauthenticated emails are managed without outright rejecting them. Once you're confident that all legitimate emails pass authentication and no critical messages are being flagged, you can move to p=reject. This final step blocks any unauthorized emails from being delivered.
During this process, make it a priority to update your DNS records, double-check your SPF and DKIM configurations, and work closely with any third-party email providers to address potential issues. This gradual transition helps enhance your domain’s email security while maintaining smooth email delivery.
What are the best ways to manage SPF, DKIM, and DMARC records for multiple domains using automation?
Managing SPF, DKIM, and DMARC records across multiple domains can become a lot easier with automation tools like Mailforge. These tools take the hassle out of setting up and maintaining DNS configurations, saving time and cutting down on human errors. Plus, they help ensure your email authentication stays consistent across all your domains.
If you’re looking to boost email deliverability and security, consider adopting some key practices: centralize your DKIM management, perform regular audits of your DNS records, and rotate encryption keys on a routine basis. By incorporating automation, you’ll create a scalable and dependable email infrastructure, making it much simpler to handle large-scale outreach efforts with confidence.